Espire IT
Managed Support Plans
Our Managed IT Services at Espire IT are designed to keep your business running smoothly with expert support and innovative solutions. We offer a complete range of services to meet your technology needs, backed by a dedicated team and 24/7 availability.
Managed Cloud & Infrastructure
Espire IT offers robust cloud and infrastructure services to ensure your data is secure and accessible, even in the event of a disaster. Our managed cloud solutions include data backup, disaster recovery, and cloud virtual servers.
Entra, Exchange, Intune, SharePoint, Teams and OneDrive
Microsoft Tenancy Support
Management and Maintenance of your Microsoft 365 environment:
8x5 Business Support Hours: Offers technical support services available 8 hours a day, 5 days a week. This typically aligns with standard business hours, ensuring help is available during critical operational times.
Managed User - Exchange & Tenancy Only (No Workstation): Manages email accounts for users without extending support to their physical workstations. This includes setting up, configuring, and maintaining email services to ensure reliable communication.
Support Ticketing Solution (Customer Portal): A customer portal where clients can submit and track support tickets. This system ensures that issues are logged, monitored, and resolved efficiently, providing transparency and organisation.
Basic Subscription Support: Provides essential support services for subscribers, including help with setup, basic troubleshooting, and maintenance of subscription-based IT services to ensure they function correctly.
Microsoft Application License Management: Manages and optimizes the licenses for Microsoft applications within your organization. This service ensures compliance, tracks usage, and helps manage costs by aligning license purchases with actual usage needs.
Email Encryption Platform (End to End): Provides end-to-end encryption for email communications, ensuring that messages are securely transmitted and only accessible to intended recipients.
Microsoft Entra ID Identity & Access Management: Offers identity and access management services through Microsoft Entra ID. This involves securing user identities, managing access permissions, and ensuring only authorised users can access specific resources.
Windows Operating System Patching: Regularly updates and patches the Windows operating systems on client machines. This ensures systems are protected against vulnerabilities and operate with the latest features and improvements.
Email Spam Filtering & Sandboxing: Provides robust protection against spam and email-borne threats by filtering out unwanted messages and using sandboxing techniques to isolate and examine suspicious emails, preventing malware and phishing attacks.
M365 Retention Policy: Implements and manages retention policies for Microsoft 365, ensuring that your data is stored and retained according to regulatory requirements and organizational needs, aiding in compliance and data management.
Email Data Loss Prevention (DLP): Enforces policies to prevent sensitive information from being sent out via email, reducing the risk of data breaches and ensuring compliance with data protection regulations.
Data Backup / Disaster Recovery
Backup solutions ensure that data can be restored in case of accidental deletion, hardware failure, cyberattacks or natural disasters:
Offsite SaaS Backup: Ensures that data from Software-as-a-Service (SaaS) applications is backed up to a secure offsite location, protecting against data loss due to localised incidents.
Data Restore from SaaS Backup: Provides the ability to restore data from offsite backups, ensuring quick recovery of critical information in case of data loss or corruption.
Onsite Server Virtualisation: Utilises virtualisation technology to run multiple server environments on a single physical server, enhancing resource utilisation and simplifying disaster recovery processes.
BDR Testing & Validation: Regularly tests and validates Backup and Disaster Recovery (BDR) plans to ensure they work effectively and can be relied upon in the event of a disaster.
Cloud Virtual Server
Offers scalable, virtualized server environments hosted in the cloud. This service provides flexible computing resources, allowing businesses to easily adjust their IT infrastructure to meet changing demands without investing in physical hardware.
Cloud Storage: Provides secure and scalable storage solutions in the cloud, enabling businesses to store, manage, and access their data remotely. This service ensures data availability, redundancy, and security.
Cloud Network/Bandwidth: Delivers high-performance cloud networking and bandwidth services, ensuring reliable and fast connectivity for cloud-based applications and services. This includes managing network resources to optimize performance and scalability.
Managed IT
Management and Maintenance of an organiation's IT infrastructure and end-user systems. This includes tasks like monitoring, updates, and support, ensuring that IT operations run smoothly and efficiently.
Comprehensive Service Desk - within SLA's
Our Helpdesk is your first line of defence against IT issues, offering comprehensive support:
Emergency Response: Provides immediate support for urgent IT issues. This service is crucial for minimising downtime and addressing critical problems swiftly to ensure business continuity.
Unlimited Remote/Phone Support - Managed Devices: Allows clients to call for assistance as often as needed without additional charges. This ensures quick access to help for any IT-related questions or issues.
Unlimited On-site Support - Managed Devices ($100 Flat Fee per Visit): Provides unlimited visits to the client's location for managed devices, a flat fee of $100 per visit. This ensures that any on-site issues can be addressed cost-effectively.
Windows and MAC Operating System Patching: Regularly updates and patches both Windows and Mac operating systems. This ensures that all devices are secure and running the latest software versions.
Third-Party Patching (Critical): Manages and applies critical patches to third-party software applications. This service ensures that all non-Microsoft software used by a business is up-to-date and secure against known vulnerabilities.
Client Success Program
Our Client Success Program is designed to align IT infrastructure with your business objectives:
Hardware / Software Quoting & Supply: Provides quotes and supplies for necessary hardware and software. This service helps businesses acquire the right technology solutions at competitive prices, tailored to their specific needs.
Asset Inventory: Keeps a detailed record of all IT assets, including hardware and software. This service helps in tracking, managing, and optimising the use of IT resources.
Strategic Planning & Guidance: We help you develop an IT strategy that supports your business goals and future growth, offering expert guidance along the way.
Lifecycle Management: Our team ensures that your IT infrastructure evolves with your business, offering ongoing support, maintenance, and improvement recommendations.
Vendor Management: Manages relationships and communications with third-party vendors. This includes negotiating contracts, handling support issues, and ensuring that vendor services align with business needs.
Exclaimer - Central Email Signature Management: This solution ensures consistent and professional email signatures across all users, incorporating company branding, legal disclaimers, and marketing messages.

Copywriting
Lorem ipsum dolor sit amet, adipiscing elit, sed do eiusmod tempor incididunt ut

Team Training
Lorem ipsum dolor sit amet, adipiscing elit, sed do eiusmod tempor incididunt ut

Website Development
Lorem ipsum dolor sit amet, adipiscing elit, sed do eiusmod tempor incididunt ut

Email Marketing
Lorem ipsum dolor sit amet, adipiscing elit, sed do eiusmod tempor incididunt ut
Managed Office Network
Our Managed Office Network services ensure your network operates at peak performance:
24/7 Network Operations Center (NOC): Our NOC team monitors your network around the clock, detecting and resolving issues before they impact your business.
Infrastructure Monitoring: We continuously monitor your IT infrastructure to ensure it functions optimally, identifying potential problems and addressing them proactively.
Documentation: Our comprehensive documentation allows for efficient troubleshooting and provides clear guidance for your IT systems.
Managed Firewall Security Service: Provides comprehensive management of firewall systems to protect an organisation's network from unauthorised access and cyber threats.
Needing Further Assistance?
Unsure of what your current IT system looks like, and needing further assistance?
Book in a time with one of our team members who will be able to work through to find the right plan for you and your team.
Managed Security
Protecting your business from cyber threats is crucial in today's digital landscape. Espire IT's Managed Security services provide comprehensive cybersecurity solutions to safeguard your IT infrastructure and data.
Managed Security Program
A comprehensive approach to securing an organisation's IT infrastructure, involving multiple layers of security measures and continuous monitoring:
End Point Protection: Safeguards individual devices (endpoints) from threats such as malware and unauthorised access. It includes antivirus, anti-malware, and other security measures.
Entra Security and Compliance Policies: Implements comprehensive security and compliance policies using Microsoft Entra. This service ensures that identity and access management meet regulatory standards and organizational security requirements, protecting sensitive information and ensuring compliance.
24x7 Security Operations Center: A dedicated team monitoring security alerts and incidents around the clock, ensuring rapid response to any potential threats.
Threat Intelligence: Collects and analyses data on potential threats to provide insights and proactive measures against emerging security risks.
Threat Hunting: Proactively searches for undetected cyber threats within the network, identifying and mitigating risks before they cause harm.
Intrusion Detection: Monitors network traffic for suspicious activity and potential security breaches, alerting administrators to possible intrusions.
Incident Response: A structured approach to managing and mitigating the effects of a security breach, ensuring quick recovery and minimising damage.
MDM and MAM for Mobile Devices and Workstations: Mobile Device Management (MDM) and Mobile Application Management (MAM) provide centralised control over mobile devices and applications, ensuring secure and compliant usage.
Vulnerability Scanning (Internal & External): Identifies security weaknesses in internal and external IT systems, providing insights for remediation to prevent potential exploits.
Security Assessment and Vulnerability Management: Evaluates the overall security posture and manages identified vulnerabilities, ensuring continuous improvement and risk reduction.
Enhanced Attack Surface Reduction (ASR): Implements advanced techniques to minimise the areas where an organisation is vulnerable to cyber attacks, enhancing overall security resilience.
Cybersecurity
Implements technologies, processes, and controls to safeguard information and ensure its confidentiality, integrity, and availability:
Multi-Factor Authentication (MFA): Adds an extra layer of security by requiring multiple forms of verification before granting access to systems or data.
MFA - Software & Project Labour Included for 365:
Provides both the software and implementation services necessary to set up MFA for Microsoft 365, ensuring secure access.
Configure Microsoft Office Macro Settings: Adjusts macro settings in Office applications to prevent malicious code execution, enhancing document security.
Restrict M365 Administrative Privileges: Limits administrative access to essential personnel only, reducing the risk of unauthorised system changes.
Email Anti-Spoofing: Implements measures to prevent email spoofing, protecting against phishing attacks and ensuring email authenticity.
Malicious Web Filtering / DNS Security: Blocks access to known malicious websites and filters harmful content, protecting users from web-based threats.
Dark Web Monitoring: Monitors the dark web for signs of compromised data, alerting businesses to potential security breaches.
End-Point Detection & Response: Continuously monitors and responds to threats on endpoints, providing advanced protection and threat remediation.
Phishing Simulations: Conducts simulated phishing attacks to test and improve employees' ability to recognise and respond to phishing attempts.
Security Awareness Training Program: Educates employees on cybersecurity best practices, enhancing the overall security posture of the organisation.
Legal Policies and Templates: Provides standardised legal documents and policies to ensure compliance with cybersecurity regulations and best practices.
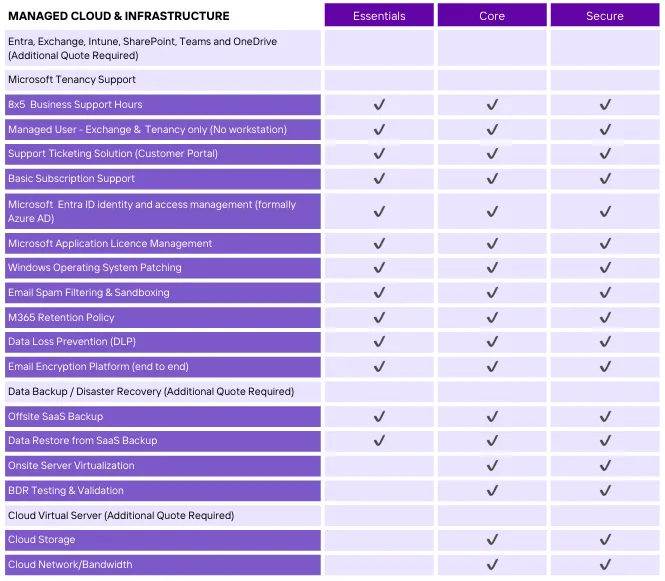
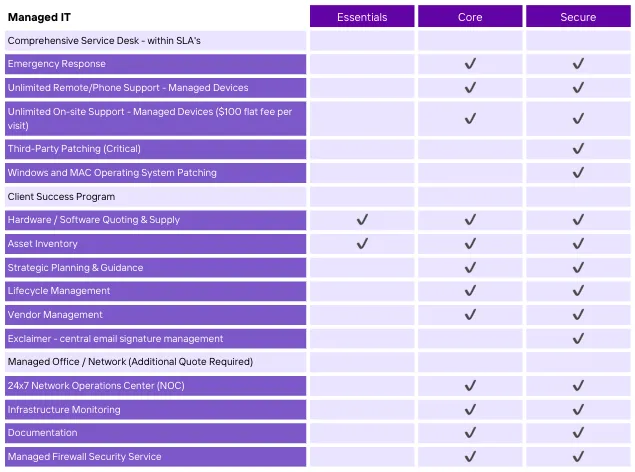
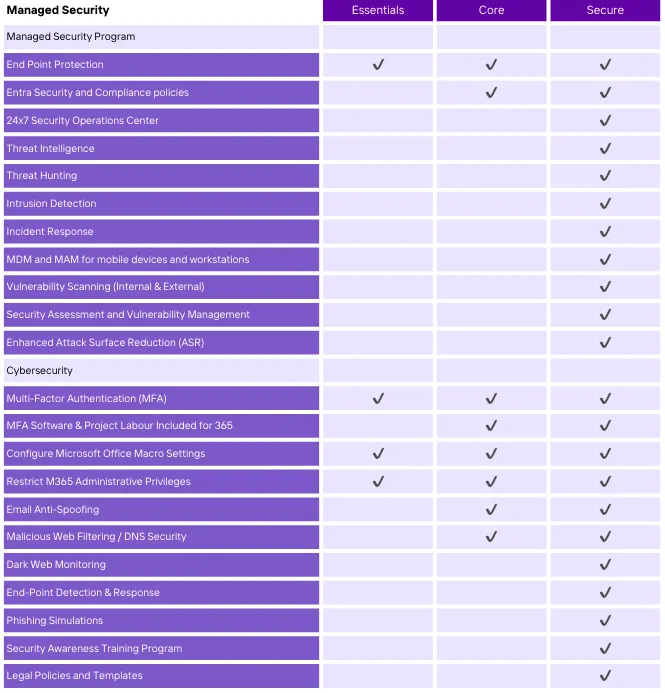
Table Comparison
See table comparison for the different plans that Espire IT offers.

FAQ
What is the main difference between Essentials and Core?
With our Essentials plan, support is limited to managing your Microsoft 365 tenancy, including user accounts and email issues. Workstation or laptop problems are not covered under this plan.
The Core plan offers unlimited remote support, which extends coverage to include issues with your workstations and laptops, ensuring comprehensive IT support for your entire infrastructure.
We’ll Show You How It’s Done
Still unsure about your current IT system and need further assistance?
Don't worry! Book a time with one of our experienced team members, and we will work closely with you to understand your unique needs and find the right plan tailored for you and your team. We are here to ensure you have the best IT solutions to support your goals.
Our success stories








We work in a space where we rely on IT systems that are secure and bleeding edge. Paul & the team look after us.
Our ability to look after our customers across multiple sites in Seymour is down to our IT systems and the team at Espire IT.
Our people are more connected than ever before and we're able to operate nationally without IT limitations.
We’ve seen significant improvements in our IT infrastructure thanks to their innovative solutions and reliable service.
Rohan Wills
Founder & Director
Greg Beer
Founder & CEO
Rob Nyhuis
Head of Operations
Melanie Milson
EA/Operations Manager

P: 1300 766 551




